Privacy Policy
Who we are
NOFRAUD is the company that develops The Fraud Explorer software. This software is registered in the USPTO patent office of the United States of America and is the intellectual property of NOFRAUD LATAM LLC (American Company) domiciled in Chicago, Illinois.
What we do
We offer a service that consists of the implementation of a methodology that allows us to detect, prevent and predict the occurrence of unethical acts, such as fraud, corruption, abuse, violence, among others, in a corporate environment. This service is offered under a monthly subscription modality and includes the deployment of our software The Fraud Explorer and advice from ACFE and ICPF certified personnel in fraud risk management.
Where we are located
NOFRAUD has its main office in Chicago, Illinois, United States. We provide our services in Colombia, Ecuador, Panama, Peru, Mexico, Chile, Argentina, Uruguay, Costa Rica, Guatemala, Dominican Republic and the United States. Our technological infrastructure is located in the United States of America and Germany.
What our service consists of
To execute our service, the client must install agents on the corporate devices assigned to the collaborators belonging to the process to be monitored (example: purchasing, treasury, commercial).
By installing the agent on devices (computers, cell phones, tablets, telephone systems), it collects valuable data for the detection, prevention and prediction of unethical activities in real time. This data is sent to a console located at the client’s premises or in the cloud and is analyzed by algorithms that we have designed based on the fraud triangle theory.
Once the data is analyzed, alerts are generated in the event of behaviors compatible with the fraud triangle theory. These alerts are analyzed by humans and a risk report is created that is provided to the client periodically.
What data we collect
Agents analyze semantic data from applications used in a corporate environment, that is, they analyze the communications that occur between employees.
The agent is designed and trained to collect the minimum information necessary to detect and prevent unethical behavior, such as the time of the event, the application used at the time, the portion of the text where the alleged unethical behavior was found, the company’s public IP address, and the sender’s username.
Data characterization
The software is designed to be privacy-friendly and to handle personal data, which is why it has a privacy-based design by default. The following data reaches our platform:
- Time: The time at which the event occurred, for example “Wednesday, October 27 at 3:17 pm”. This time is captured from the time provided by the operating system.
- IP Address: The public IP address of the client company’s router, for example “200.20.23.1”. This IP address is captured in the process of sending and receiving data on the cloud or local platform.
- Sender: The username of the sender of the message as a pseudonym, for example “rgcrioses”. This data is captured from the operating system.
- Application: The name of the application in which the event occurred is captured, for example “Microsoft Teams”. This data is captured from the name of the process that is currently being used by the user.
- Event content: the portion of the text that contains the allegedly unethical behavior is captured, for example “let’s do a good deal, I select you as a supplier and you pay me a commission.”
In this document we will refer from now on to how we manage this data and what security measures are implemented to ensure its protection and correct treatment. The Fraud Explorer software is not intended to capture personal data, however, due to the nature of data analysis, it may occur that an event contains personal data.
Channels being monitored
The Fraud Explorer supports the selection of channels to be monitored and does so based on the name of the applications. The client, at the initial stage of the project, informs us of the corporate applications used by his company and the need for monitoring all or some of them. For example, the client may state the need to monitor Microsoft Teams and Outlook.
Depending on the client’s regulatory environment and jurisdiction, for example if it is a SEC-regulated trading department, the applications that must be monitored have a broader spectrum, regardless of whether they are for corporate or personal use. For this case, we put together a list of applications where there could potentially be semantic content, such as Telegram, WhatsApp, Messenger and Gmail.
Restrictive profiles
The Fraud Explorer allows the configuration of roles and profiles with various objectives. One of them is to prevent a person accessing the platform from viewing personal data, masking names and other types of data that are considered personal. The platform has the administrator role, the viewer-only role, the event marker role, and the event auditor role.
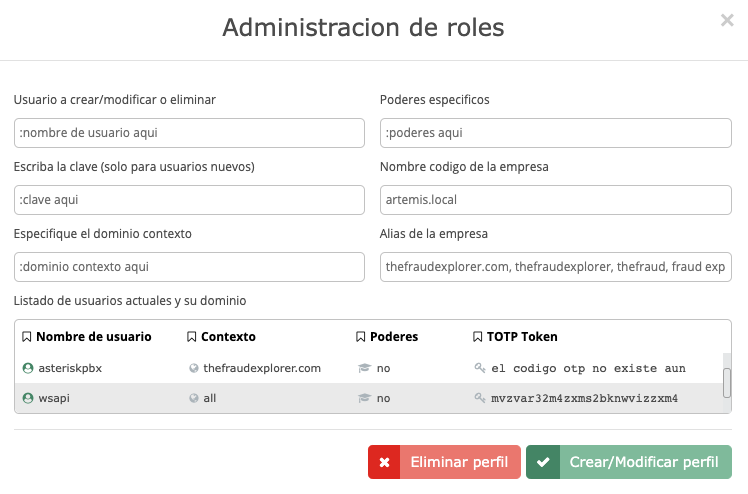
Authentication
The Fraud Explorer supports the use of a username, password, captcha code and time-based OTP code. This means that multiple authentication factors are used to access the platform.
Monitoring schedule
The Fraud Explorer allows monitoring schedules to be set. Even though our clients have an acceptable use policy and state that devices do not belong to employees, employees often violate the policy and use the devices for personal and intimate purposes. We encourage our clients to communicate that the expectation of privacy on their devices is well defined, however, to be privacy-friendly, The Fraud Explorer allows monitoring schedules to be set, so that employees have non-monitoring time that they can dedicate to their personal activities.
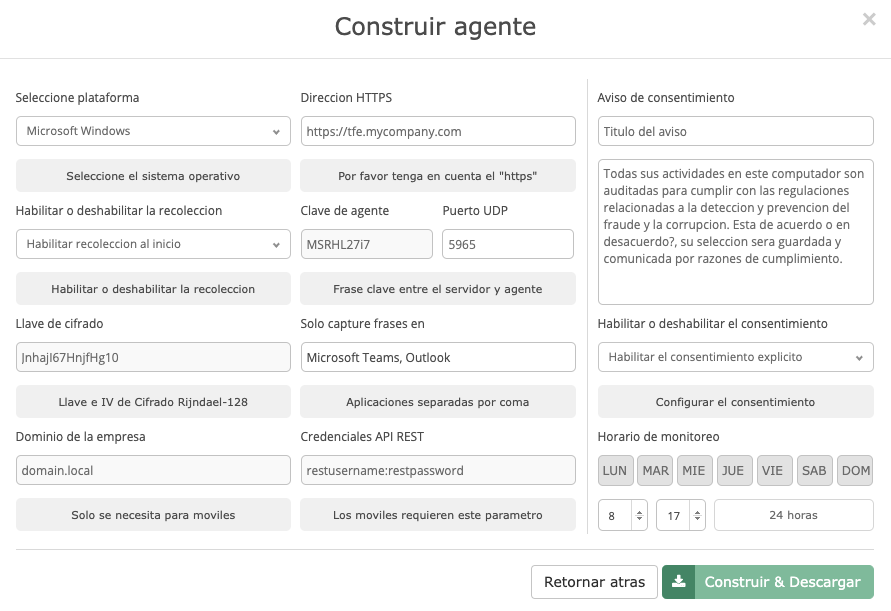
Request for consent
The Fraud Explorer allows a monitoring prompt to be set and the employee to be asked for explicit consent, which will be requested when they log in to their device and before the actual monitoring starts. This consent is saved in our cloud or local platform to have evidence of the day and time when the employee did or did not give consent for monitoring.
Off-line monitoring
The Fraud Explorer only monitors when the employee is online working on corporate applications. When the employee is not online, the monitoring system does not send the data that is being analyzed in real time.
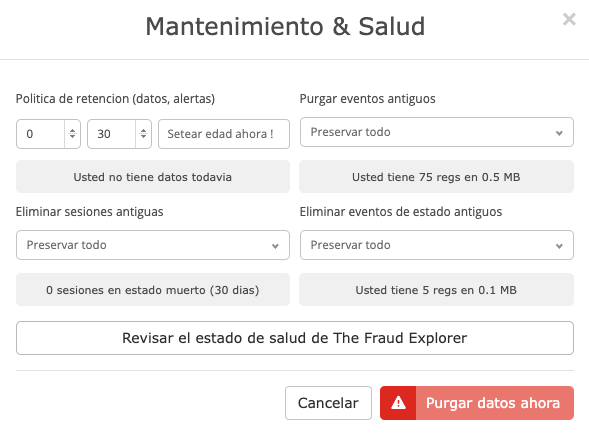
Data retention
The Fraud Explorer establishes policies for the retention of all of your data. One is the data retention policy for information that comes from agents and another is for events or alerts that are generated on the cloud or local platform. By default, the retention of data coming from agents is zero, this means that once that information is processed, it is not saved. For events, we recommend that a retention of 30 days be maintained, that is, fraud and corruption alerts will only have a life of 30 days on the platform and after those 30 days they will be safely deleted.
Restrictions on data export
The Fraud Explorer only allows data export to Excel. This type of export is done to prepare the risk report that is delivered to clients periodically and contains alerts for unethical behavior. Only a person with the specific role and profile can open this report, which is password protected.
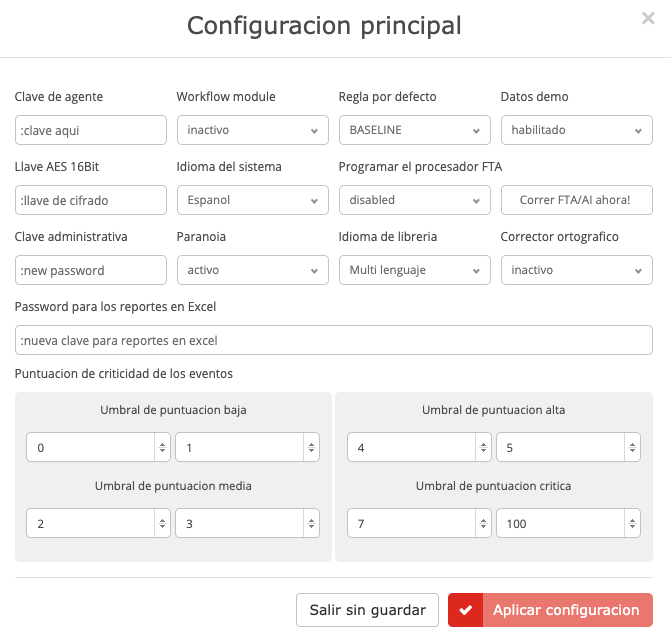
Data encryption
The Fraud Explorer encrypts data in transit and at rest using a variety of algorithms and mechanisms. The agent sends data to the cloud or on-premises console via TCP and UDP protocols, each with AES-128 encryption, plus additional layers of protection such as HTTPS. Once data is at rest, it remains encrypted in the databases.
Data erasure
The Fraud Explorer allows data to be deleted in two ways. One is autonomously, on one’s own initiative, for example when an employee is no longer employed, or the other is when an employee exercises his or her right over his or her data and requests that all information remaining about him or her on the anti- fraud platform be deleted.
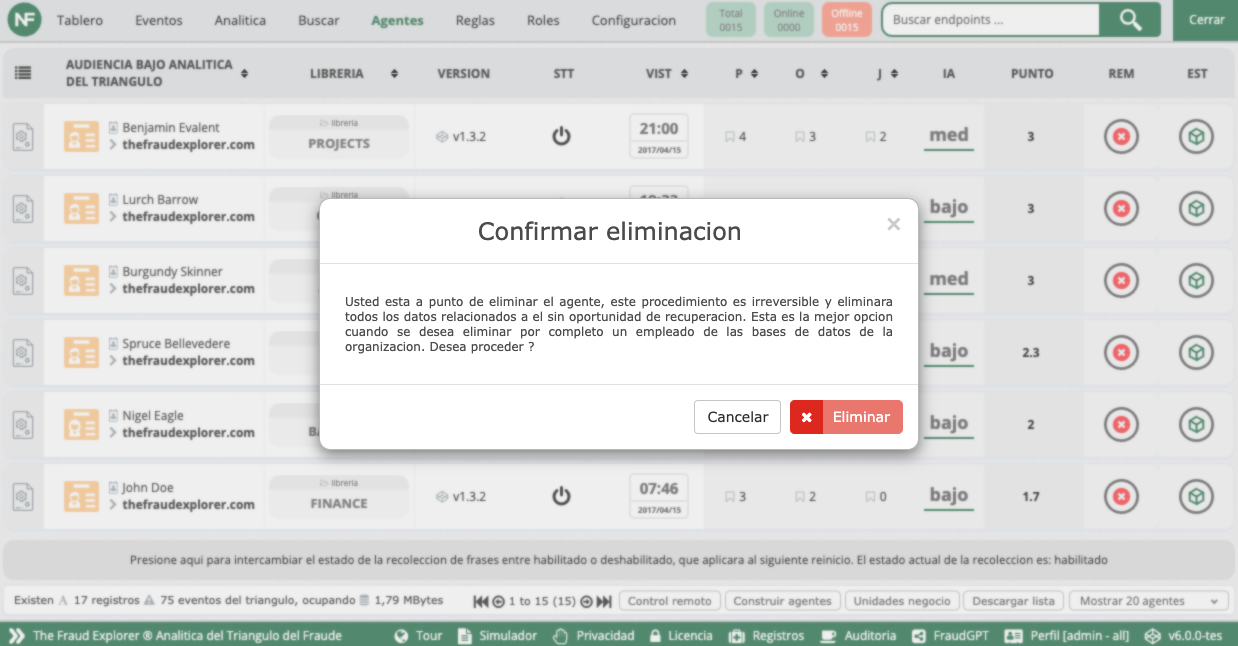
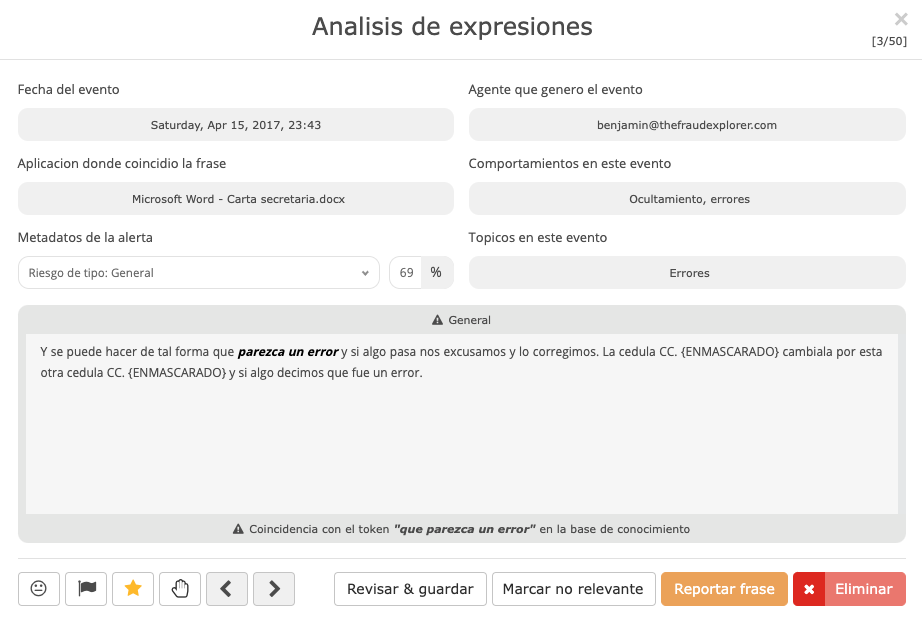
Data masking
The Fraud Explorer has a special data masking process carried out by an independently operating artificial intelligence. This AI is trained to search for names, identification numbers, bank details and other data that may be considered sensitive, to mask them so that not even an administrator can see them.
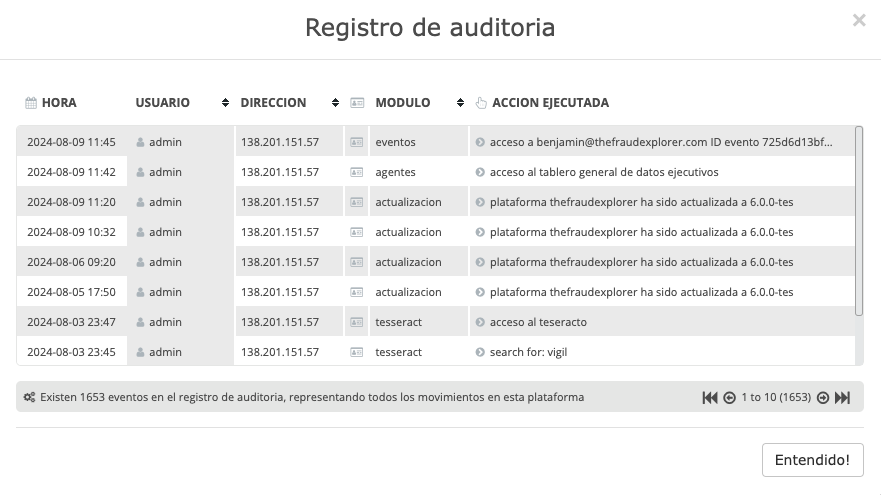
Audit log
The Fraud Explorer records all actions executed on the platform for all roles and profiles and allows them to be consulted in a special module called “Audit”. This module is so detailed that it even records searches performed on the platform, not only the movements made by a user.
Safety in design
The Fraud Explorer uses the ISO27k framework as the basis for its security design, complying with all the controls recommended by the standard. In addition, we also use the CIS (Center for Internet Security) controls for each of our information systems to ensure their security. We have an annual security assessment and we carry out ethical hacking tests and penetration tests on a monthly basis for each of our clients’ instances. We decided to follow the best practices of the European Parliament’s GDPR and apply all the recommendations to our The Fraud Explorer software.
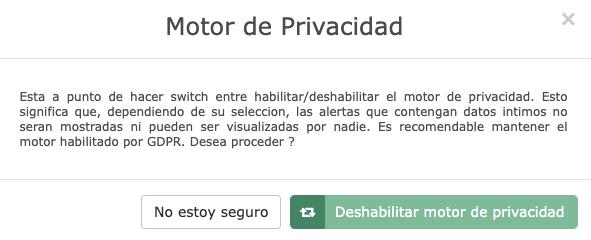
Privacy
The Fraud Explorer incorporates an independent artificial intelligence that is located at the front line of data processing and its function is to detect intimate content in communications. If detected, this content is ignored immediately and is not even collected, processed or analyzed by the other algorithms.
Right of access
NOFRAUD has provided a platform to address requests related to the processing of personal data. You can access it at help.nofraud.la and create a ticket indicating that the reason is “Data Privacy”.
Differential privacy
Calculations performed through algorithms limit the personal information that reaches them in order to reveal a result. This means that inferences of probable internal fraud focus on processes and not on people, even though the information produced by an employee is analyzed, the detection focus is associated with the action and not the subject.
Policies
NOFRAUD has developed the information security policies (which also contains the incident management policies and business continuity policies) and the personal data policy. All these policies are available for our customers and regulators.


