FraudGPT, the most advanced AI platform to predict human behavior
Awarded in Europe by the World Compliance Association as the best anti-fraud solution in the world and recognized by ACFE in the United States as the most impressive technology based on the Fraud Triangle theory, we proudly present a consolidated version of the capabilities of our technology, built in Colombia, expanded to the United States and developed by three people, Marta Cadavid, Daniela Echavarría and Julián Rios, which today helps the largest companies in the world to prevent and detect unethical human behavior in real time.
The Fraud Explorer is a unique software which has been deployed in large companies in many countries of different industries such as Retail, Energy, Oil & Gas, Healthcare, Insurance services, Banking, Financial, Food production, Airlines, Construction and Services
Our technology has reached companies in Colombia, Panama, Ecuador, Argentina, Uruguay, Peru, Costa Rica, Haiti, Chile, Puerto Rico, Mexico and the United States and deployed in highly regulated environments with several clients listed on Wall Street to support their anticorruption strategy for regulators such as SEC (Securities Exchange Commission) in the United States.
Scientifically supported technology
Our technology was created with a methodology based on the semantic analysis of the communication channels used in the corporate environment to ensure behavioral compliance by modeling the Donald Cressey’s Fraud Triangle Theory.
The well-known concept has three components that combined lead to fraudulent and human behavior risks: Motivation/pressure, perceived opportunity, and rationalization of committing the fraud or crime.
We put together the Fraud Triangle theory with AI, data analytics, and semantics to understand in real time human behavior through corporate communications when employees have the intention to do something wrong in the workplace. We created The Fraud Explorer.
We have been studying the Fraud triangle theory since 2013 to understand human behavior. We also know 15% – 25% people will never be involved in unethical or dishonest behaviors. Unfortunately, the large % of people act according to the moment, situation, or crisis. It means, each organization deals with a high and permanent risk. Dishonest and criminal conducts always are revealed through red flags which are related to personal and financial pressures, opportunities created by the perpetrator or lack of company controls, rationalizations when the person justifies the means, technical capacity to do something wrong, and influence of internal and external cultural factors.
The Fraud Triangle theory has been the most important foundation in our company since the methodology encompasses anthropological studies to explain why people commit unethical acts in different geographies and cultures. We know the simple analysis of conversations to look for suspicious behaviors with poorly said words or phrases related to insults, violence, sexual harassment or crime do not solve the real problem of unethical human behaviors. That’s why we combine the richness of the Fraud Triangle theory with artificial intelligence, data analytics, and semantics to analyze corporate communications to take a proactive approach by helping corporations to determine the motives that highlight employees’ decision to commit fraud, opportunities that empower them to perpetrate the act, and rationalizations as a good person living in a bad moment.

The methodology based on the Fraud Triangle theory is built and work to predict, prevent, and detect unethical human. Otherwise, the process to search for phrases or words will not have a reliable ooutcome. For instance, clients who currently use The Fraud Explorer are able to identify unethical employees, possible problems in the early stages, uncover schemes, mitigate monetary loses, and address faster investigations or in the best cases making quick decisions before the damages happen.
Besides Donald Cressey’s Fraud Triangle theory as a foundation of our methodology, the academy sphere has been the beginning and support for our company through the validation process of our work by the research teams of two universities: the University of Alabama and the Israel University of Technology, who were able to understand our technology goes behind and beyond of the searching phrases industry to land on the most sophisticate software to predict the human been intention in the corporate arena.
An intelligent methodology, not just an intelligent AI
Since the same unethical behavior has different repercussions when it occurs in HR or IT departments and even in different industries, the understanding of human behavior is a substantial factor for us as a company. Consequently, our methodology was built with a segmentation of human behaviors where the layers of artificial intelligence pursue different typologies of wrongdoings that tremendously affect the corporate environment such as conflict of interest, illegal medications sale, or information linkage to leave aside the simplicity of only detecting words and suspicious phrases in corporate conversations.
Our technology automatically classifies the type of behavior that has occurred plus its context, topic, corporate risk, probability and impact which is the real value that a strong anti-fraud solution can offer to improve the compliance environment and address investigations quickly. A simple surveillance or communications surveillance tool without any foundation may not be enough to face real problems with shareholders and even regulators.
Our company has incorporated several artificial intelligences into this entire process. The first artificial intelligence determines the best type of data to process (at origin). The second one determines whether the data complies with the regulations and limitations of each country / jurisdiction regarding privacy and personal data. The third artificial intelligence anthropologically determines the relevance based on the Fraud Triangle theory, and finally the last AI based on the generative model applies attention to the context with a reinforcement learning on more than 100 thousand cases of fraud capable to determine whether only if the alert is true or a false positive.

The world’s most compatible anti-fraud technology
We have been developing different analysis mechanisms for unstructured data during the last ten years. Today, our technology offers three types of solutions for data acquisition and processing: agent-based, agentless, and eDiscovery type.
-
Agent-based: we support the installation of agents for PC, Mac, Cell Phones, Tablets and IP Telephony Systems, with support for Windows, Mac OSX (intel and M), Linux, Android and Asterisk operating systems. Under this model, we support the acquisition of data in real time, also using artificial intelligence to find the best possible data, in local and web applications such as Outlook, Gmail, Yahoo, Slack, WhatsApp, Facebook Messenger, Instagram, Twitter, Signal, Skype, Teams, Zoom, Webex, Word, Excel, PowerPoint and other applications considered by the client and necessary for monitoring such as SugarCRM, Salesforce or even SAP. In conclusion, our AI makes it possible to monitor any application on a PC and Cell Phone.
-
Agent-less: we support connection through APIs to third parties such as Microsoft 365, Slack and Google Workspace allowing corporate communications to be extracted in real time for analysis without the need to deploy agents.
-
eDiscovery: we provide delayed-time analysis of data such as PST and Documentation (PDF, XLS, DOCX, PPTX) through desktop forensic applications that we have developed and make available to our clients at no additional cost. In addition, we have designed an API for our clients to submit their own data and take advantage of the power of our AI.
We are detecting deviant human behaviors with the greatest spectrum and scope possible to promote prevention and detection as effectively as possible through multicultural, multi-language, and multi-operational AI trained with the culture of 21 countries.
The most affordable anti-fraud technology
We are committed to do our best for our clients. Our affordable prices allow a client with 50 thousand employees to monitor all of the communications generated in its company without disruption and data collection. We know it sounds incredible, and that’s why our service-based business model is tailored according to each client’s risk; therefore, the number of agents, processed alerts, information channels, or data size are not relevant to determine the price of our solution. We solve real problems!
Since we have optimized data processing and analytics tremendously, we offer to our clients a flat/plain price, regardless of the type of company, the number of employees or the complexity of their data. Thus, our technology is the favorite tool for auditors, compliances officer, human resources teams and C-Levels executives because of the reliable and quality services and the reasonable price. We have created the opportunity to any company to have the best AI to anticipate the human risk.
We work very closely with our clients through a holistic strategy on the tough task of preventing and detecting unethical behaviors in real time. We provide to the client our best people, design project processes and deploy the best anti-fraud methodology in one package avoiding complicated processes regarding the infamous number of licenses.
Focusing on service, not technology
We do not sell software and we do not license agents. What we do is accompany our clients in the task of preventing and detecting unethical behavior in real time.
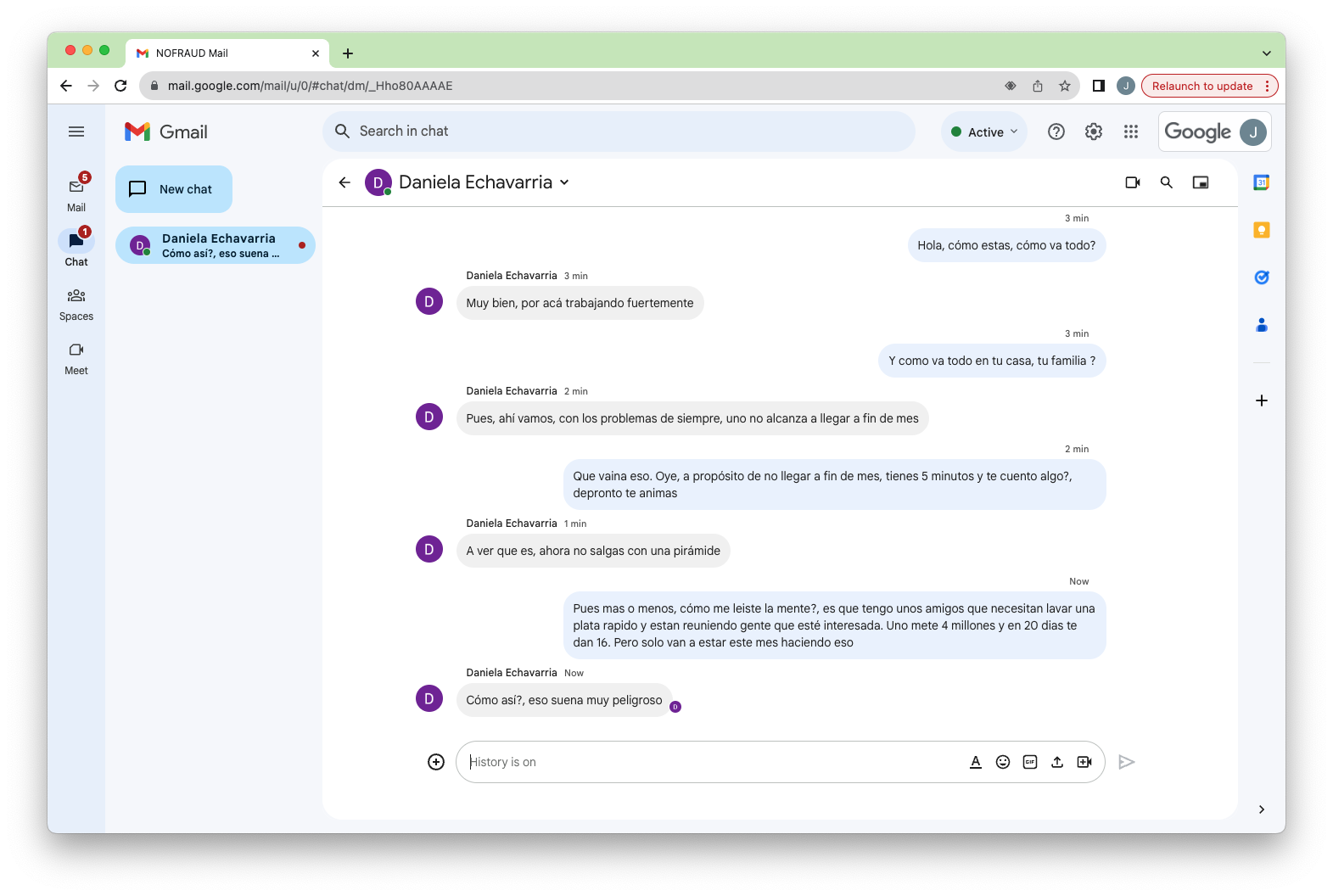
Due to our service consists in full support and commitment to our clients to detect suspicious behaviors in written communications, we go further to fill the clients’ expectations with key factors, as follow:
- Once our technology is deployed, a fraud risk diagnosis based on COSO is performed. This risk diagnosis will reveal the areas of the company with the most urgency in the application of the Fraud Explorer to concentrate the efforts and gain time.
-
With our team of engineers, ethical hackers and information security professionals, we determine with the client where to place the technology. Our company supports the on-demand and on-premise model. Choosing one or the other does not bring any additional cost to our clients. This step allows the client to choose the information that will not be transmitted outside of the corporate systems, at any time and in any phase of the application of artificial intelligence.
-
With our team of anti-fraud and anti-corruption experts, we determine the relevance and materiality of the alerts to classify and fully understand their meaning.
- With our team of investigative and forensic experts, we help the client to determine the best procedure to convert an alert into evidence to be presented in a legal process, if needed.
- Our team assists and supports meetings with the client’s legal teams at no additional cost to build legal cases related to compensation due to the damage caused in the event that the alert and its investigation have determined material or moral damage for the organization.
-
We help our clients in the design of new internal controls to prevent, from occurring again, unethical conducts detected through our methodology and with our team of experts in fraud risk management based on COSO.
It is our technology, not a third party tool
Nowadays, most artificial intelligence companies depend on the use of third-party models, and even worse, these companies depend on sending their data to sites where it is processed (API), breaking or mistreating the confidentiality of information and personal data processing.
Our technology is 100% developed in-house by our engineers. The final layer of generative artificial intelligence is trained by our own staff and resides on our own servers to protect the best interest of our clients regarding to the sharing or losing information issues. Our clients are fully informed and aware that their information will not be shared with anyone, not with Open AI, not with Google, not with Microsoft, not with anyone else.
For our most demanding clients in transmission and transfer of personal data, we support the deployment of 100% of our methodology including all layered AI in their own facilities. The fact that we own the 100% of the technology allows us to customize and execute the project according to the client’s expectations to provide to legal teams and boards of directors’ peace of mind regarding the security of the company’s information from third parties.
We have a server farm in our datacenter with NVIDIA technology specifically designed to enhance the processing of neural networks and generate answers to the questions about unethical behavior for our clients alerts.

Each alert generated by our methodology contains an analysis based on the Fraud Triangle theory to determine its relevance and the probability of materializing. Next, a typology of fraud is automatically applied to that alert (i.e. conflict of interest), followed by a risk typology (i.e. financial risk), and a behavioral classification (i.e. stress, fear). Finally, generative artificial intelligence is responsible for evaluating the context of the alert to determining whether the alert has sufficient parameters to be considered a real alert and discard the false positives.
Several processes are involved in the alert’s generation, as follow:
-
The AI finds the best possible data to capture based on the employee’s interaction with business applications or communication’s channels
-
The AI determines if the analyzed behavior refers to the employees’ private lives to rule it out, or if the found behavior contains sensitive personal data (i.e. credit cards or passwords) to be discarded or masked.
-
The AI conducts a sentimental analysis to find neutrality, positivity or negativity of the behavior. This part of the process is vital to find usefull information and events related to violence, sexual harassment, xenophobia, discrimination, racism or a negative workplace environment.
-
The AI that performs an analysis of honesty by analyzing behaviors and contexts. Aside from the Fraud Triangle theory, some studies have shown people reveal their honest or dishonest behavior through certain forms or types of communication. This type of alert is very valuable to predict or determine the probability of a dishonest conduct.
-
The AI applies the fraud triangle algorithm to determine, according to anthropological studies, the different aspects of human behavior to predict an unethical act, find and differentiate the relevance of such conducts since the alerts have diverse relevance.
-
The generative artificial intelligence has been trained with 56 billion parameters and focused on text analysis that encompasses untruthful characteristics. This AI has been re-trained by our team of engineers using reinforcement learning with more than 100 thousand cases around the world.
The methodology and the above process run in real time. The employees’ communications (voice and writing) are analyzed thanks to the robust IT architecture and software built with neural network processing with cluster platforms and NVIDIA card farms.
The largest behavioral spectrum on the market
Our technology is trained with AI to detect unethical behaviors such as conflicts of interest, illegal gifts, bribes, sexual harassment, misappropriation of assets, reports manipulation, violence, stress, anxiety, disloyalty, unfair competition, data leaks, concealment, mental health issues, economic pressures, drug abuse, anomie, money laundering, terrorist financing, travel expenses abuse, fines, lawsuits, fraud, personal businesses, dishonest trading, altered inventories, inadequate valuations and up to more than 90 classifications of unethical activities and immoral actions.
Our technology automatically identifies the type of behavior, risk type, probability of materializing and the relationship with other employees in the company. The methodology supports several workflows with artificial intelligence to connect and condition its deductions to certain patterns previously defined by the client such as “keep me informed of unethical situations that occur in relation to supplier XYZ, with person X from the treasury department and person Z from the procurement department”.
False positives are no longer a problem
The technology applies several layers and various types of artificial intelligence (expert systems, Bayesian and generative) to trigger the alerts. Each alert passes through a rigorous automated testing until it is ready to be presented to the client as relevant with “sufficiency” which consists in having the enough data to answer questions such as Who?, Where?, How?, What? and Why?.
The best team in the world
Expert fraud examiners, developers, ethical hackers, data scientists, information security experts, forensic experts and anthropologists are what make our great company and work team a reality. We have traveled the world showing our technology from Switzerland, India, Spain, Australia, the United States, Israel, and in Latin American countries from Mexico to Argentina.

We invite you to contact us, we are more than happy to tell you more about our technology and how we can help you detect and prevent unethical behavior in your organization.
References
(Donald Cressey, 1953) The others money, the fraud triangle.
About NOFRAUD
NOFRAUD is the company that develops The Fraud Explorer anti-fraud software and supports people and companies to face and solve their challenges regarding internal fraud, corruption and corporate abuse. NOFRAUD has created the largest behavioral database of dishonest acts in the world in Spanish and English, which helps artificial intelligence find suspicious patterns of corruption within organizations.

We improve the capacity of organizations by increasing their profits, taking away from perpetrators the possibility of negatively affecting income through fraud, corruption, corporate abuse and the generation of toxic environments..
Contact with me at » jrios@nofraud.la and Reach us at » www.nofraud.la.



